SAML SSO
Share KeePass Passwords with your Team of multiple users
Password Server allows Single Sign-On (SSO) from your trusted Identity Providers such as: Azure AD | Microsoft Entra ID, Office 365, and ADFS.
KeePass SSO simplifies login for users and allows integration with other applications. Users can sign-in once to a Trusted Identity Provider and not be prompted again when using Password Server.
SAML is a standard, popular security framework for Single Sign-On and there are many notable services which are compatible as Identity Providers (IdP). Authentication tokens are exchanged using SAML 2.0.
Applies to: Versions 7.9.9+, Enterprise+SSO
Have Questions? Contact Us!
Supported Identity Providers
| Microsoft Entra ID (formerly Azure AD) | AWS |
| ADFS | Office 365 |
| OKTA | Google Apps / G Suite |
| Shibboleth 2.0 | F5 |
| Ping Identity | Salesforce |
| RSA SecurID Access | Entrust |
| OneLogin | MicroFocus (NetIQ) |
| OneIdentity | Gluu Server (open source) |
| SecureAuth |
… as well as many other compatible SAML Identity Provider services!
Are there other integrations you use, would like to use, or that you have questions about? Contact Us!
References:
- Wikipedia: SAML-based products and services
SAML SSO Configuration
Available guides through some popular integrations, and additional guides will be added in the future:
SAML SSO Features
SSO for KeePass
- KeePass users will not be re-prompted to login when already signed-in to a trusted identity provider.
SSO for Web Application
- Web application users will not be re-prompted to login when already signed-in to a trusted identity provider.
SSO for Auto-Fill Plugin
- Chrome Auto-Fill plugin users will not be re-prompted to login when already signed-in to a trusted identity provider.
Enforce SSO Authentication
- Require interaction with a Trusted Provider before accessing Password Server.
Separate Local Emergency Access
- Administrators still have a local method to sign-in.
Enforce SAML SSO Login
(Versions 7.10.9+)
Password Server can restrict and enforce users to sign-in only by SAML SSO authentication to a configured provider.
Both Web application and KeePass users can use single sign-on authentication.
This feature is beneficial when requiring MFA authentication or requiring other identity verification factors specified outside of Password Server.
Settings to Enforce Single Sign-On
Settings for Enforcing SSO partner sign-in can be found under Policy Administration Global Settings page:
- User and Roles > Policies
- When "Enforce Partner Sign-in" is set to true, users will be required to log in to Password Server through a configured SAML Authentication partner.
SAML Single Sign-On:
- To configure a SAML Single Sign-On partner, see:
Allow Exceptions for Direct Sign-in
Enforcing sign-in through a partner can be great for managing everyday user sign-in but in some instances we may want allow exceptions for admin users to be able to sign-in directly to the Password Server.
This can be set in either the Default Policy or individually or role managed policies. When the above "Enforce Partner Sign-in" is set to true, we can set to "Allow Exception for Direct Sign-in" in one of these policies.
- User and Roles > Policies > New or Edit Policy > Authentication Policy
- From here we can set the "Allow Exception for Direct Sign-in" to True and users or roles who have been assigned this policy will have the option to sign-in directly to the Password Server application.
Bypass SAML SSO in an Emergency with Direct Sign-In
In order to login locally and bypass SSO Partner sign-in, you will first need to make the policy exceptions above, then you can access the direct sign-in URL:
- https://localhost:10001/Account/SignIn/Direct
Replacing the localhost value with the correct server domain.
Changing SAML SSO Certificates
(Versions 7.11.9+)
Certificates include private encryption keys which help to generate the secure encrypted connection between the server and your other devices. It's important to keep the keys safe as they work to decrypt the encrypted connection and safeguard access.
New certificates should be generated periodically, which helps protect the system in the case the keys should be lost or stolen.
Upload the Partner Configuration Certificate
Upload the public certificate from your Identity Partner system by editing the SAML Partner Configuration and uploading the certificate file from your Identity Provider.
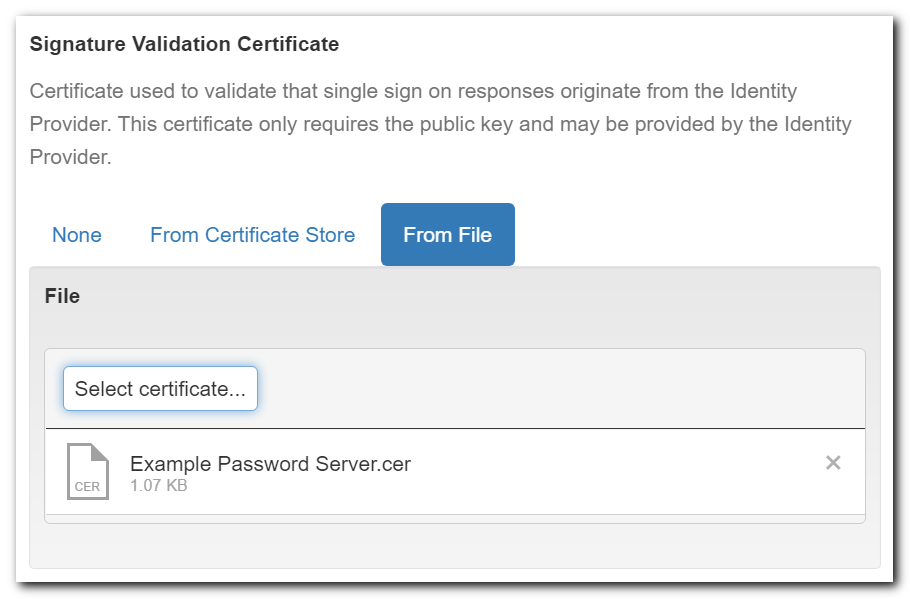
For more details on where to find this Certificate, see details in SAML Guides:
Upload the Site Certificate
(Optional) Upload your site's private certificate (.pfx file) by editing the SAML Configuration.
- This is needed if using Single Log Out (SLO)
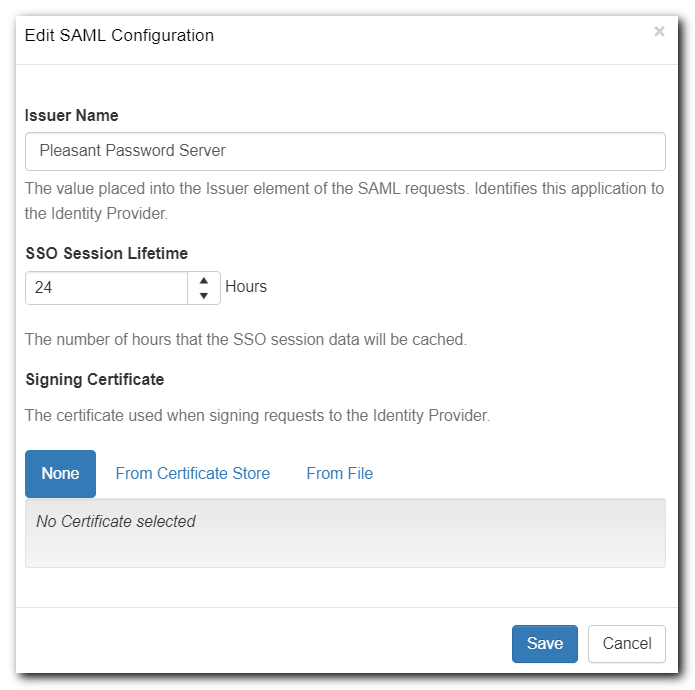
For more details on about this Certificate, see details in SAML Guides (SAML with AD FS, SAML with Microsoft Entra ID (formerly Azure AD)).
